Table of Contents
Your cloud project, the beginning
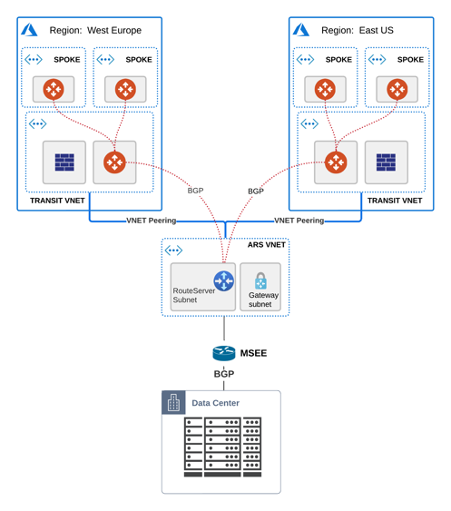
You deployed your highly secure & encrypted Hub & Spoke model in Azure ( with Aviatrix), scaled up the environment and expanded into additional regions.
Next you want to migrate your workloads from OnPremise and empty your datacenters (does Cloud first sound known to you?)
You require a link with low latency for your sensitive apps (SAP, Databases) and good throughput/performance so you choose an Express Route circuit and deploy an Azure Route Server (ARS) to handle the routing information exchange between the 2 worlds.
Everything comes up seamlessly and by this time your design should look similar to this:
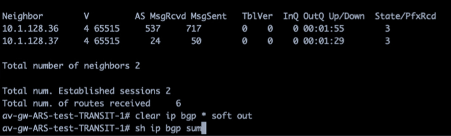
The BGP sessions of one of the Aviatrix Transit NVAs to the two legs of the Azure Route Server:
SPOILER:
The Azure Route Server is in fact 2 x VMs which require full mesh BGP connectivity.
If you have only partial, meaning each Avx Transit with just one leg of ARS, then you go into unpredictable/undocumented Microsoft behavior whereas 50% of your traffic can be blackholed => NOT cool
More workloads migrate to the cloud, you assign additional CIDRs to your VNETs and at some point in time when adding a new CIDR you notice an interruption in your OnPremise traffic.